Malware as a service (MaaS) is a malicious software delivery model adapted from the legitimate software world where many applications providers use various distribution methods to make software accessible to end users over the internet.
You certainly have seen, or been a user of, a software distribution model like software as service (SaaS) such as Google Workspace, Dropbox and Salesforce; infrastructure as a service (IaaS) such as DigitalOcean and AWS; platform as a service (PaaS) such as Heroku and AWS Elastic BeanStalk; and others. Many of these services offer free trials, pay-as-you-go and low-cost monthly subscription plans while also making it easy for customers to scale their usage up or down as needed. Vendors, of course, then use data collected from their large user bases to improve products and offerings.
Now malware developers are following similar routes, making the MaaS black market as popular and competitive as the conventional SaaS market. All it takes is savvy marketing to build a MaaS revenue stream, distribute to users and then cull data to innovate with new features that can continue to evade detection and security measures. The anonymity of this criminal activity also contributes to the popularity of MaaS where only the most successful deployments stay active, but others that have seemingly “died” can be easily re-organized, re-branded and re-deployed.
The Malware as a Service Landscape
As with aboveboard businesses, malware as a service creators need to advertise their services somewhere. Some choose clearnet websites to host pages that describe the malware’s functionality, pricing models, methods of purchase and contact information. Others prefer posting on hacking and other underground forums to communicate with prospects via post replies or direct messages. A recent example is this information stealer malware ad found on a hacking forum.

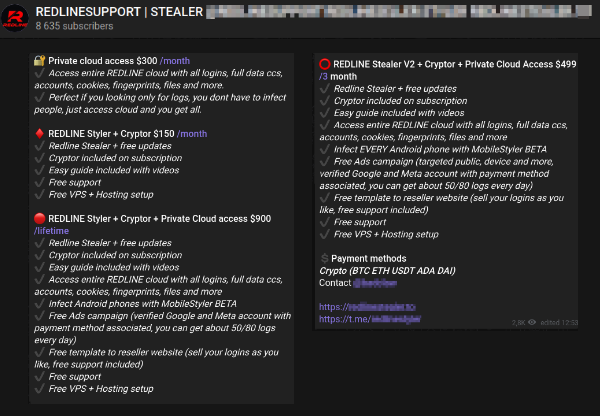
Another very common contact method is via Telegram. This instant messaging service allows criminals to anonymously create a communication channel with their customer base and use features such as end-to-end encryption, channel conversation moderation, chatbot automation and the ability to upload up to 2GB-sized files, among others. The Telegram screen shot below advertises a popular MaaS threat known as RedLineStealer with all the functionality an unskilled threat actor might need, such as support, guides, and a Virtual Private Server ... all included in subscriptions that can be paid via various cryptocurrencies.
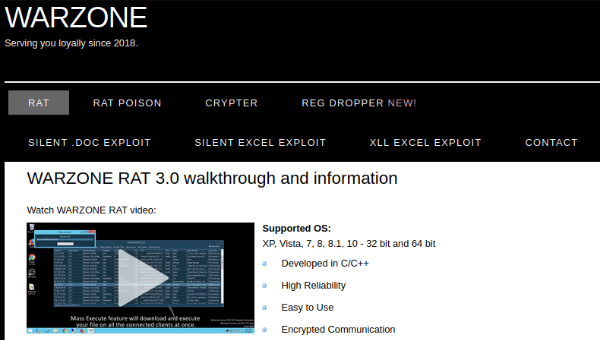
And here is a different type of malware, a remote access trojan known as Warzone RAT with many malicious capabilities, hosted on a dark web site:
Malware as a Service Characteristics
As cyberthreats evolve, cybersecurity solutions also evolve to stay ahead of the bad guys. So, when a new MaaS threat is created, its fundamental goal is to evade and hide from the offensive threat hunting and proactive defensive measures of targeted organizations. Anti-virus solutions, for example, will try to scan the file or a code loaded directly in the memory using various methods and techniques to look for suspicious characteristics or behaviors. That’s why a malware campaign needs to use creative methods to make payloads undetectable by intended victims ... at least for a little while.
This process of making malware undetectable is known as FUD (fully undetectable) payloads. Each malware sample or file is nothing more than a sequence of bytes that will be loaded into a target’s operating system when requested by a user or another program. Payloads in the context of cyberattacks refer generically to malicious content, regardless of the method used to distribute or hide it.
To create undetectable malware, or FUD payloads, cybercriminals often purchase programs to hide malicious content delivered to victims via social engineering. The way to hide it depends on the program:
- Protector: protects malicious code from being analyzed and scanned using different techniques, such as obfuscation, packaging, virtualization, anti-debugging, anti-hooking, etc.
- Crypter: Stores the malicious code encrypted and decrypts it after a runtime.
- Binder/Joiner: Embeds malicious code inside an installer or other legitimate program.
- Builder: Generates the executable file or script responsible for executing the main payload using protection, encryption and union methods.
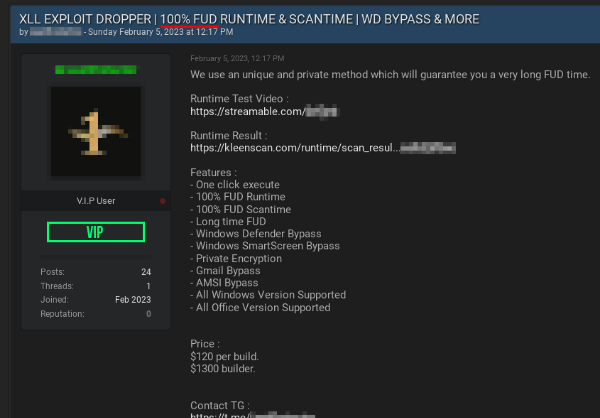
These FUD programs are also offered as a service so criminals can turn their malware into FUD payloads. It is common to see these different types of programs offered simply as "builders" with mixed "crypter" or "protector" capabilities. The following example is a protector advertised on a hacking forum as 100% FUD, suggesting it avoids detection by most anti-virus engines.
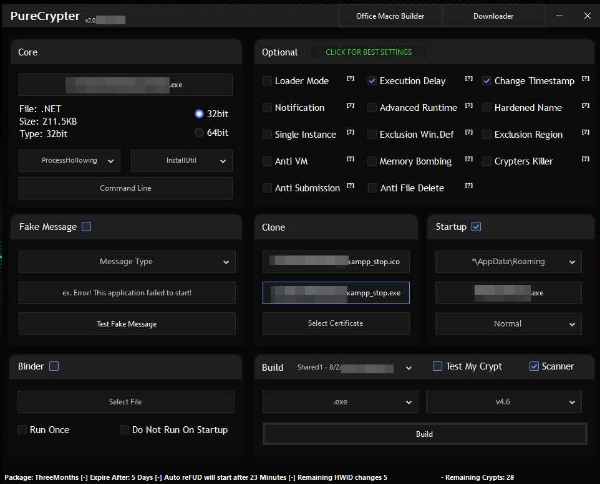
And here is an example of an advanced crypter program used to customize malware to make a FUD payload:
These characteristics are what differs a popular MaaS from other types of cyberthreats advertised on hacking forums. Criminals will seek the ones which make their malware campaigns last longer, resulting in infecting as many devices as possible. MaaS threats often include a builder/crypter as part of a subscription plan to retain their customer base and also help the MaaS developer troubleshoot the effectiveness of their FUD process.
Additionally, some MaaS developers are focused solely on providing these builders/crypters/protectors with constant updates and affordable pricing as depicted in this screenshot showing crypter offered as a product on an e-commerce platform.
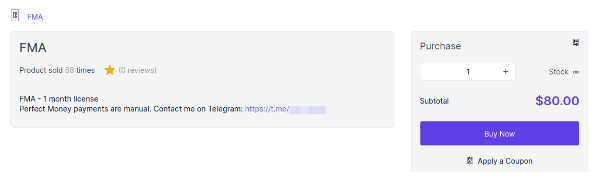
Because some of the techniques to protect a program from being scanned or copied can also be used by legitimate software, it is not uncommon to see crypters offered on the internet as a generic protection service for any type of software, disguising their malicious purpose and preventing them from being copied or removed by legal action.
Accordingly, this is how attackers use malware as a service platforms to execute cyberattacks. Some of these services may not truly offer everything advertised, but since most of their customers are inexperienced criminals, it doesn't make much difference because, at the end of the day, some degree of success can be achieved even in campaigns without a FUD payload.
Appgate’s Threat Advisory Services Malware Analysis and Research Team (MART) frequently monitors trends like MaaS and its implications to keep you up-to-date on emerging threats. Learn more about our world-class Threat Advisory Services offerings here.
Additional Resources
Blog: Replit: From Work Tool to Phishing Instrument
eBook: Staying Ahead of the Evolving Threat Landscape
Analyst report: Appgate Named Tech Leader in Quadrant Knowledge Solutions 2022 SPARK Matrix
