Consumers have become increasingly reliant on digital platforms to complete daily tasks and access sensitive data. This means that threat detection strategies must dynamically respond to user behavior in real time. A risk-based strategy that protects consumers throughout every phase of the fraud lifecycle is the strongest approach to preventing targeted attacks.
Fraud lifecycle explained
The fraud lifecycle is a three-step process that most attacks follow.
- Targeting: the initial launch of an attack, where fraudsters identify a target and attempt to compromise credentials or take over a device.
- Launching: the attacker gains access to a user’s device or account.
- Cashing out: sensitive information or money is stolen.
Most fraud schemes share a common goal, which is to complete the cashing out phase of the lifecycle. Protecting your organization and your consumers against these threats requires a risk-based approach, but not all solutions are created equal.
Vulnerabilities in fraud protection solutions
Many organizations rely on multiple solutions from different vendors to protect against targeted fraud schemes. In our most recent Faces of Fraud report, 31% of security professionals reported that they lacked the appropriate technology to detect and respond to security incidents.
There are a few issues with fraud protection solutions that can significantly weaken an organization’s security posture:
- Black box approach: various solutions digest information and produce a risk-score without any real data or user analysis. The black box method provides a one-size fits all approach making it difficult to identify and respond to fraud.
- Rules-centric: rules are useful in certain cases but applying a static set of rules to all consumers hinders fraud defenses. It doesn’t account for real life situations based on individual user behavior.
- Siloed analysis: relying on multiple solutions that can’t or don’t communicate prevents any real-time action or analysis, which is an ineffective approach.
A strong solution combines machine learning with contextual data to identify fraud in real time.
A layered approach to fraud protection
With fraud schemes in constant motion, a layered approach is key to protecting your organization and your customers. Fraud prevention tools that communicate, make a significant impact in detection and response times.
Appgate’s Risk-Based Authentication (RBA) solution provides robust protection against targeted attacks at the user level. RBA combines strong authentication with transaction monitoring through orchestration. This layered combination enables real-time action against fraud while providing a frictionless customer experience.
How it works:
Authenticate
- Strong authentication means removing or limiting the username/password combination when authenticating users. It uses advanced authentication factors and device analytics to determine that the person attempting to access their account is who they say they are before granting access. Authentication is then granted or denied with a high level of confidence.
Monitor Transactional Activity
- Using machine learning, Appgate’s transaction monitoring dynamically identifies unusual behavior at the user level. It identifies malicious activity in real-time based on various factors such as date/time, location, transaction amount, device risk and more. Transactions can be blocked or challenged in real-time, preventing account takeover.
Orchestration Workflows
- Using data from login attempts and transactional activity, organizations can create customized workflows that are easily adjusted through a drag-and-drop interface. This enables you to automate responses to malicious behavior based on your risk tolerance.
This is an example of Risk-Based Authentication in action starting with a transaction:
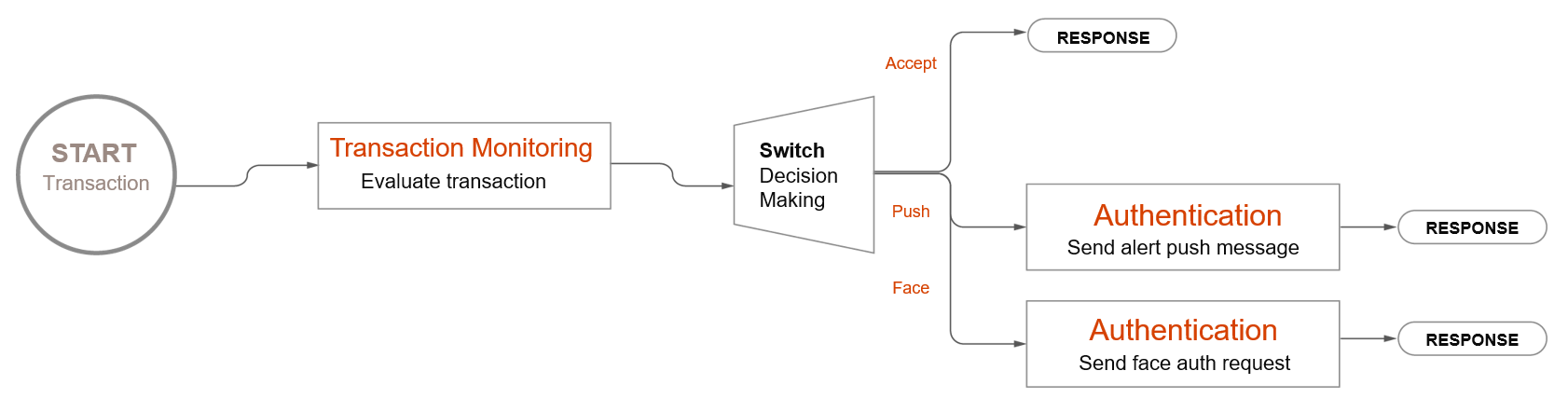
The image is an orchestration workflow that can be easily adjusted based on an organization’s needs. In this example, the transaction begins and is evaluated. Based on that evaluation, the user is either allowed to transact, or must be authenticated to proceed.
These orchestration workflows are highly customizable and remove the burden of back-end configurations needed for solutions to communicate.
Time to reevaluate fraud protection
The ever-evolving fraud landscape means organizations must constantly reevaluate existing solutions to ensure that they can keep up with new attack techniques. There’s no magic bullet when it comes to protecting your organization against fraud. The most effective method is a layered approach that can respond to real fraud in real-time.
To learn more about how Appgate can strengthen your security posture and streamline fraud management click here.
[1] https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf
