One notable free hosting site is replit.com, which is similar to GitHub and encourages support among developers by allowing them publish work that becomes accessible to anyone who wants to learn and compare processes. However, it has become a favorite target for cybercriminals, according to analysis by our Digital Threat Protection (DTP) SOC team. In fact, in 2022, 55% of phishing attacks detected in the Americas were on replit.com. And in January 2023 alone, there were a total of 4,409 detected attacks, more than 300 times the value reported for the same period in 2022.

Identifying evasive maneuvers by cyberattackers
After continuous study of replit.com, our DTP team proactively developed tools, strategies and identification protocols to find scenarios and anticipate evasive maneuvers used by cyberattackers to avoid being detected on the platform. One of the most notable maneuvers is the creation of blacklists to reject access from certain IPs ... whether they belong to certain automatic detection systems of malicious sites such as dedicated web portals and antivirus software, or IPs that do not belong to the same geolocation as a user target.
Another common threat actor method is to reject any connection coming from a search engine such as Google, Yahoo! and DuckDuckGo, among others, or to display fake error screens to create routes that are hidden from search systems.
These types of maneuvers make it easier for bad actors to remain undetected and allow better victim profiling to ensure a greater number of effective attacks. The flowchart below shows the logic behind a phishing attack where decision points establish where the attack is executed correctly or canceled according to evasion maneuvers. The potential victim is a user of the attacked entity who has been filtered by the anti-detection system under aforementioned standards (IP, origin, country of entry, etc.).
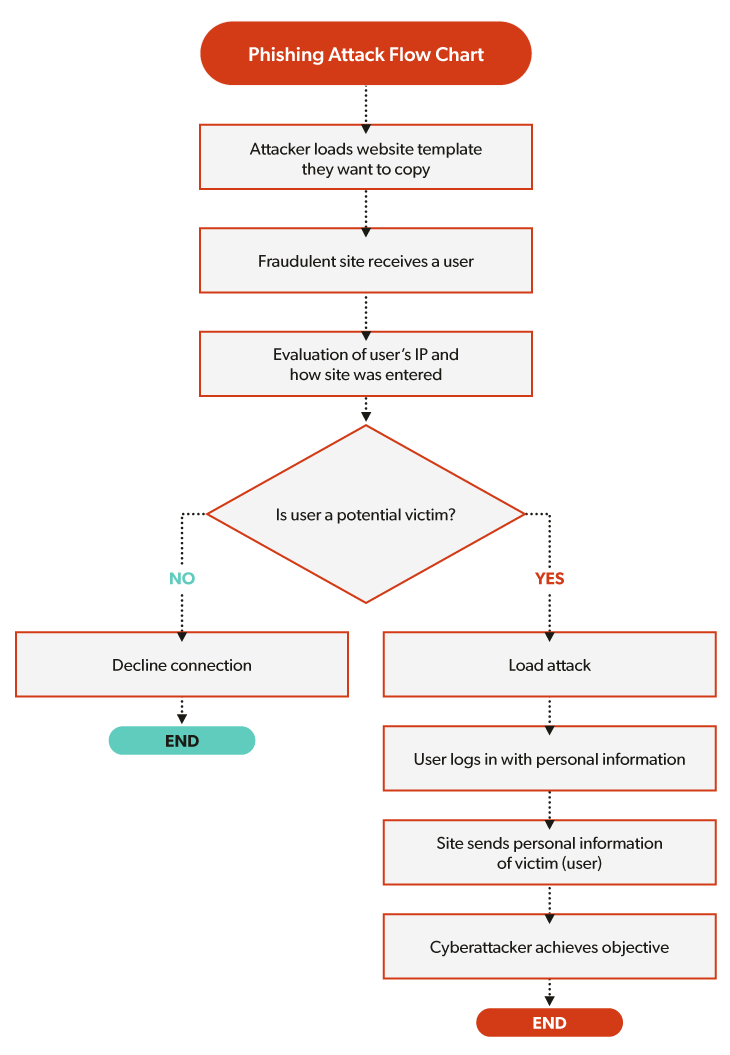
Tools to detect and deactivate cyberattacks
The continuous study of replit.com has led to development of tools and protocols by our DTP SOC analysts to accelerate detection and deactivation of attacks before they are successful, especially on sites where sensitive information such as credentials, username, or even IP and city of the affected user could be publicly accessed.
In recognition our work, replit.com named Appgate as one of its few Trust Reporters to set up more effective notification channels and reduce deactivation times to just a few hours. The increase in volume of cyberattacks also led replit.com to reinforce authentication and verification processes for its new users in order to mitigate fraud scenarios.

Avoid become a victim phishing
These types of internet cyberattacks and evasion maneuvers are imperceptible by unsuspecting end users. So, to ensure fewer people fall victim to ever-changing cybercriminal strategies, here are recommendations to avoid falling for phishing:
- Avoid entering pop-up windows that include promotions, offers or any type of information that does not come from official sources, and if you’re not sure, contact the entity directly
- Do not directly enter a site using links that come through non-official channels, such as emails, text messages, among others
- Always check the domain of the entity you want to access
- Keep your browser's security options active, especially when accessing transactional portals such as banking and other financial institutions and online retail sites
Phishing is one of the most commonly used types of attacks in the world of fraud and constantly evolves using free platforms as an easy means of access for this purpose. That is why Appgate takes measures to keep up with cybercriminals. We are very proud to be recognized as one of the few replit.com Trust Reporters, which, in turn, allows us to continue protecting our customers more effectively.
Additional Digital Threat Protection resources
Data sheet: Appgate Digital Threat Protection Overview
eBook: Staying Ahead of the Evolving Threat Landscape
Video: Digital Threat Protection by Appgate
